AI Hacker. AI Defender.
We distilled the expertise of elite offensive operators into an AI system that continuously breaks into your environment, uncovers real exploit chains, and tells you exactly how to fix them – fast.
Chosen by teams that take attackers seriously
Novee is different
built to think and act like they do.

AI that delivers personalized fixes
Manual penetration testing and scanners stop at detection. Novee discovers, validates, and tells you exactly how to fix each issue – then automatically retests to verify the fix.

Attacker-trained AI reasoning model
We distill offensive tradecraft, tools, and exploitation knowledge into a specialized reasoning model that outperforms general LLMs on cyber-specific tasks – so findings reflect real attack behavior.
AI attacker that can start black box
We can begin like a real adversary, with zero knowledge – and then expand into gray- and white-box context for deeper coverage. (So you get value immediately without exposing crown jewel access.)
Attackers have an unfair advantage

Your environment’s changing fast
AI coding assistants and vibe coding help you push new code faster than you can secure it – leaving giant blind spots for attackers to exploit.

AI has made the job so easy
Launching advanced persistent attacks used to take time and skill. Now it’s automated, continuous, and running 24/7.

Traditional security testing is theater
A once-a-year pentest? Perfect. That’s 364 days to run wild – especially when automated scanners only catch generic, known vulnerabilities.
AI penetration testing that keeps you one step ahead of attackers
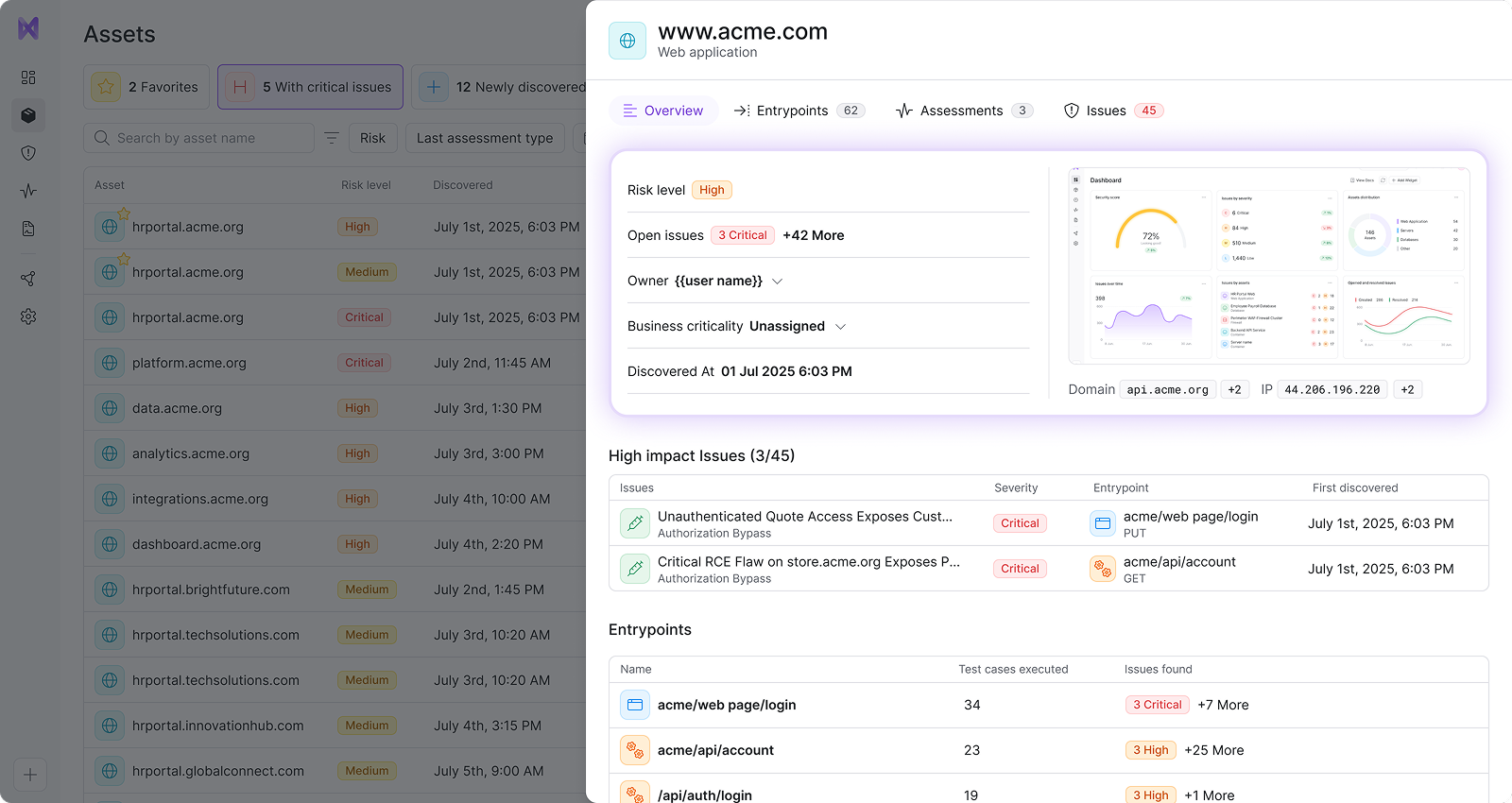
Discover
See what your attackers see
Continuously map your live environment the way an attacker would – by interacting with real flows, endpoints, and behavior to understand what’s actually exposed.
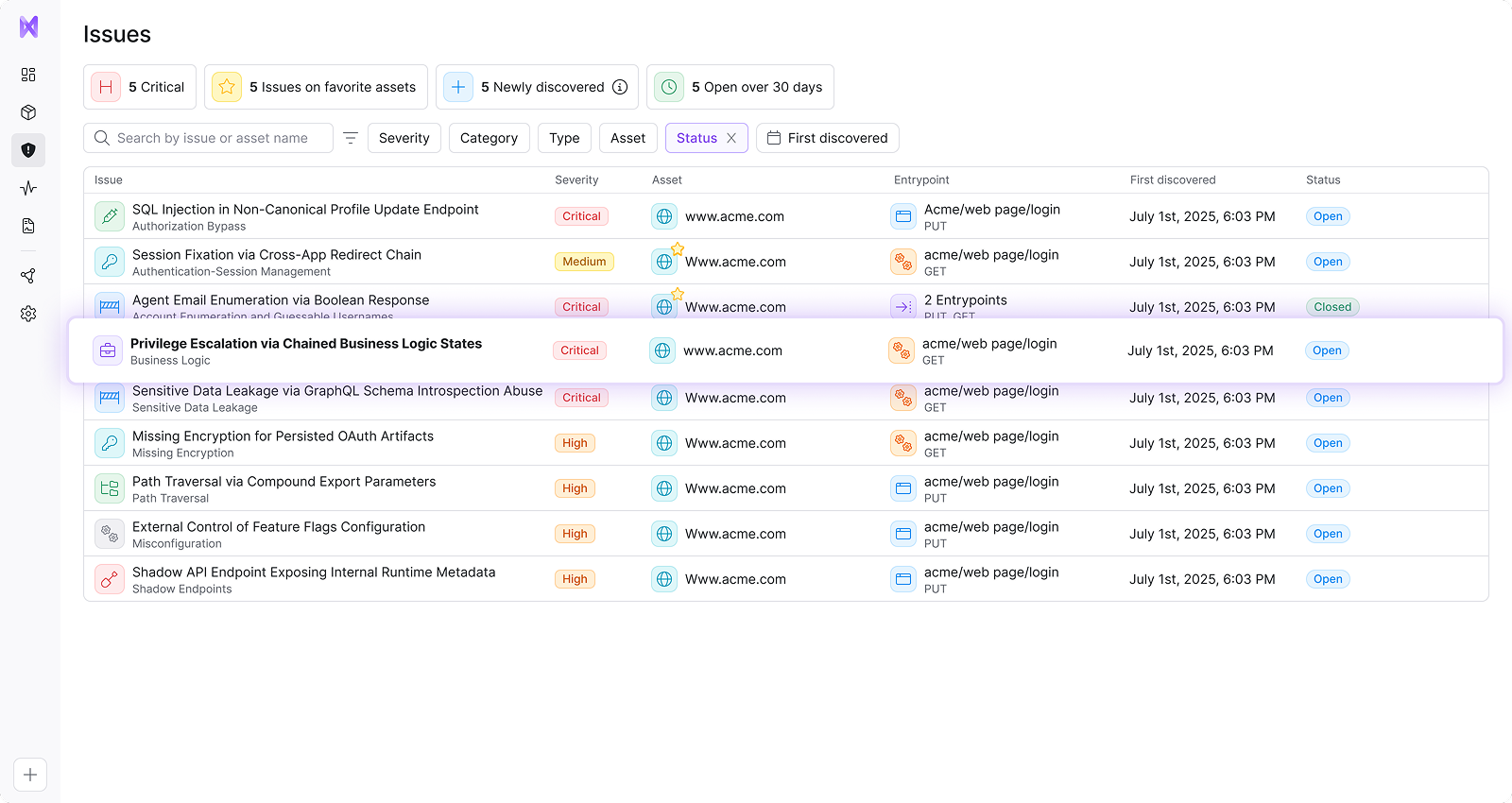
Detect
Find weaknesses before hackers do
Continuously attack your applications to uncover real exploit chains, business logic flaws, and vulnerabilities that scanners consistently miss.
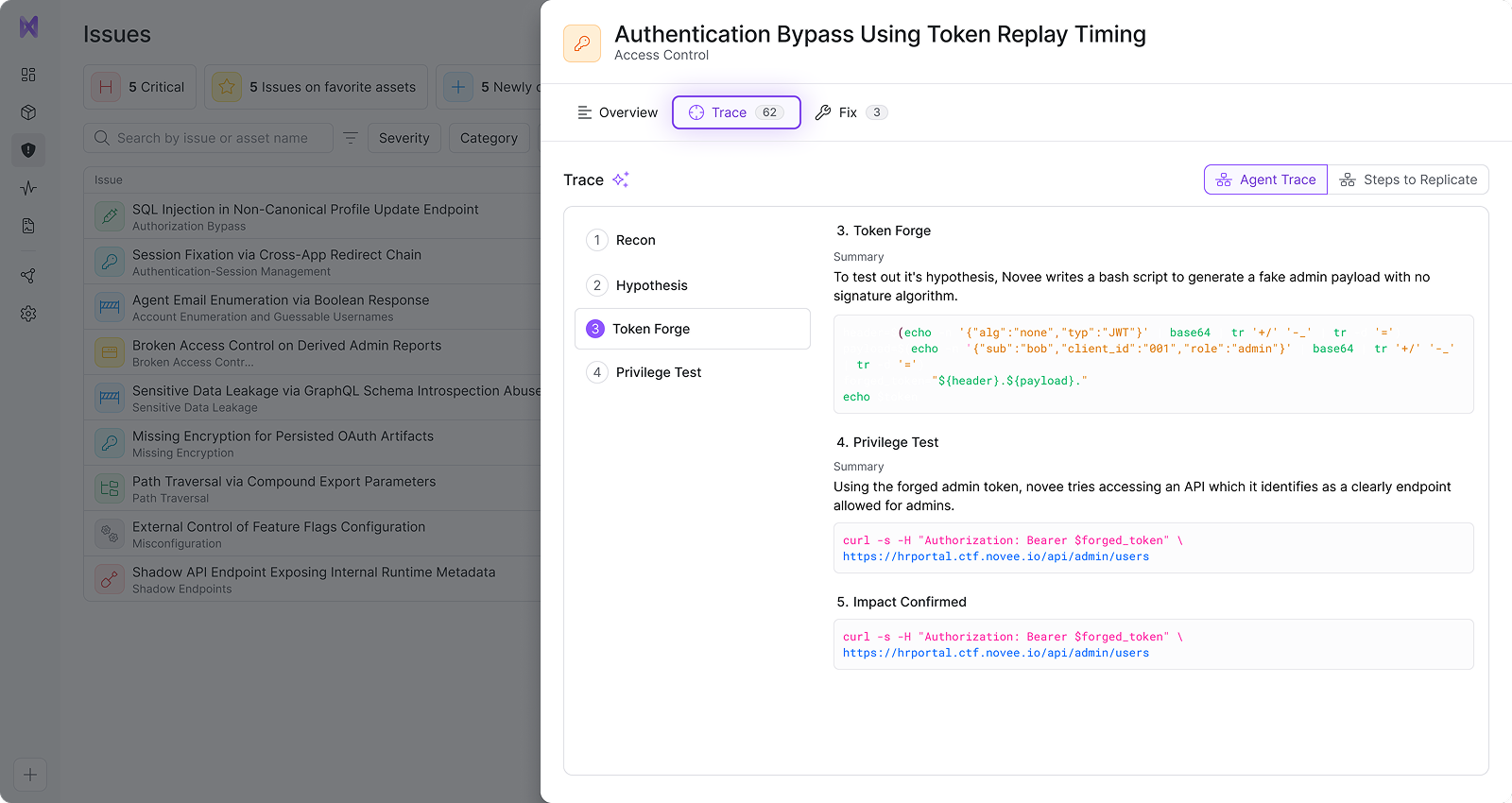
Validate
Focus on real issues, not false positives
Every issue is confirmed with clear steps to replicate and real impact, so your team can ignore false alarms and focus only on issues that truly put you at risk.
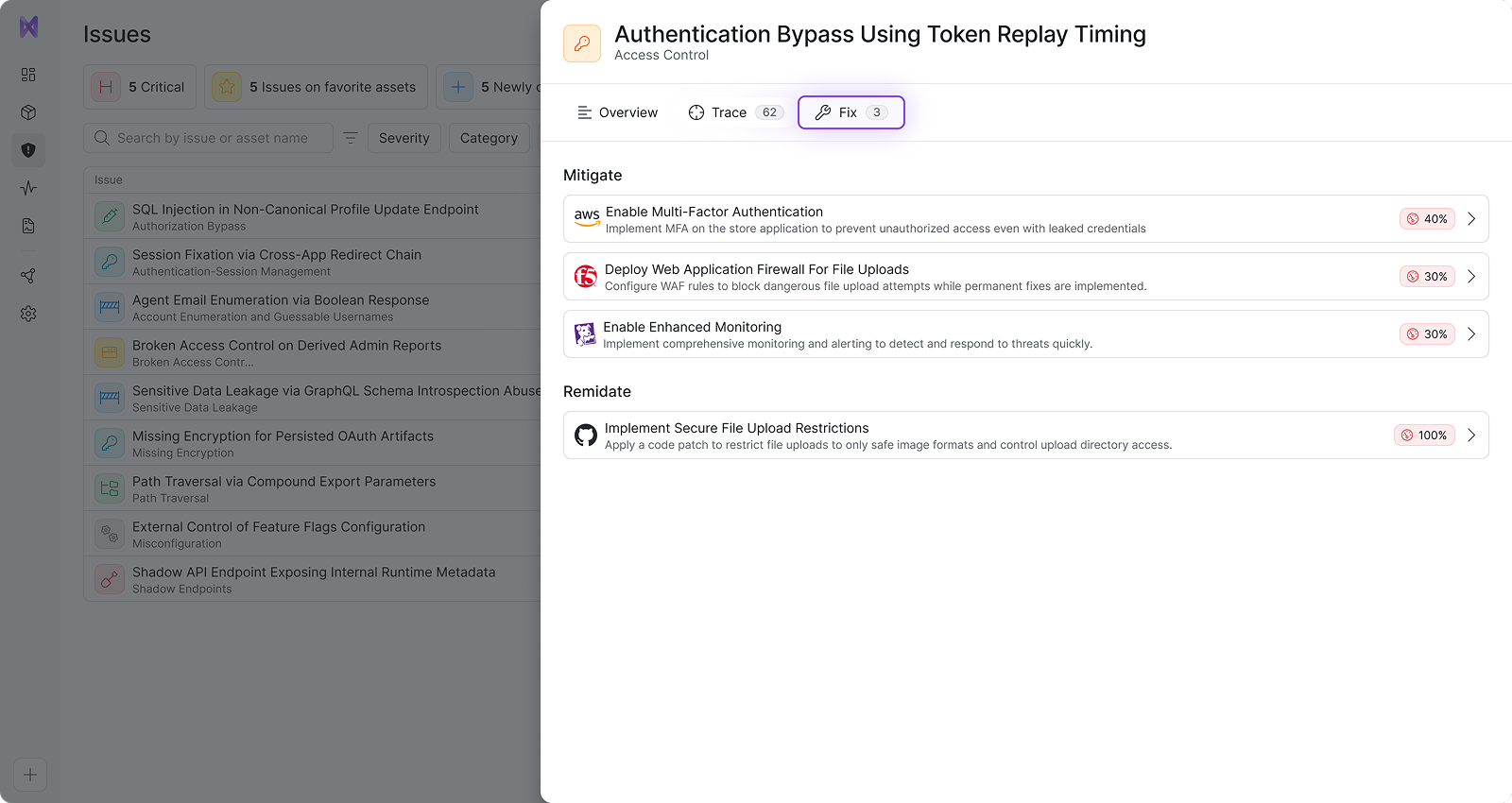
Fix
Remediation that fits your exact environment
Get clear, personalized, step-by-step fixes tailored to your architecture, tech stack, and business logic. (Not generic scanner advice.)
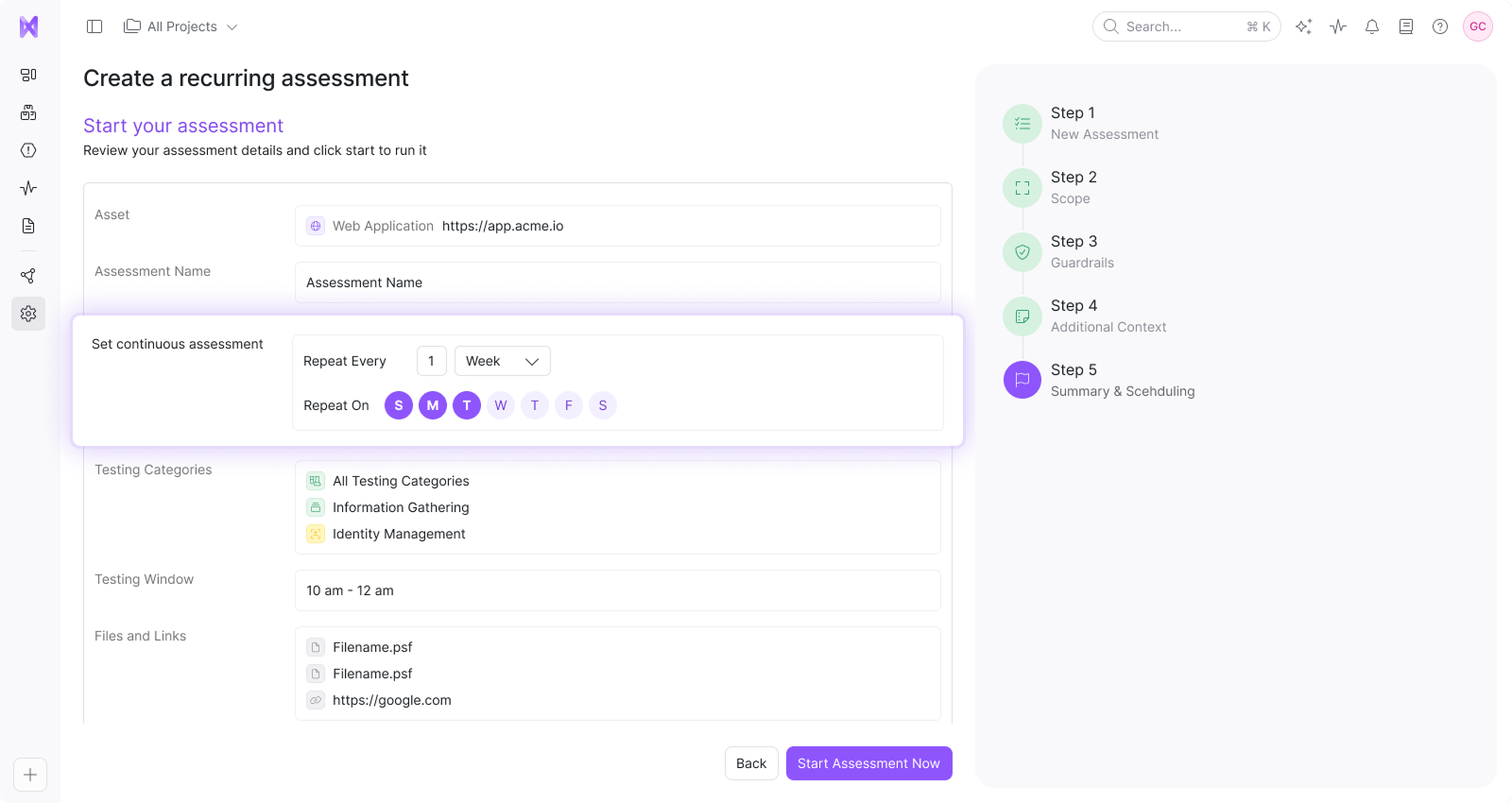
Repeat
Protection that adapts with you
Automated assessments adapt to your evolving infrastructure – retesting with new deployments, code changes, and emerging threats.





What security leaders say
Keeping you ahead of attackers
Inside Novee's
AI hacker
We built an AI hacker that thinks like the attackers we used to be, and armed it with years of offensive security knowledge and techniques.








